GPG keys and how to use them - we explain on our fingers
contents.title
- What is GPG?
- History
- Keys
- Symmetric and Asymmetric Encryption
- Kleopatra. A simple and convenient option on Linux,Windows,Tails.
- Kleopatra. Installation on Linux
- Kleopatra. Installation on Windows
- Kleopatra. Key creation
- Kleopatra. How to find your public key and save it
- Kleopatra. How to find your private key and save it
- Kleopatra. Message encryption
- Kleopatra. Message decryption
- Kleopatra. Receiving encrypted messages from other people
- What is the easiest way to transfer your key to another person
- Kleopatra. Sending an encrypted message
- Kleopatra. How to create a password-protected message
- Kleopatra. How to sign a message
- Kleopatra. File encryption
- Kleopatra. Key Backup
- Kleopatra. Publishing the public key on the server

It is a cryptographic program for encryption and digital signature.
GPG is based on the idea of two encryption keys for each user. Each person has their own private key and public key. The public key can decrypt the information encrypted by the private key.
How does it work?
So, if you want to send a secret message or file to someone, you use their public key to encrypt the information. Only the owner of the private key can decrypt it.
Public key exchange allows you to communicate securely. You can encrypt your messages with your conversation partner's key, and he decrypts them with his private key. And vice versa.
A private key is also able to sign files like a digital signature. This can be verified using the public key.
- 1997: Werner Koch, a German programmer, developed GPG (GNU Privacy Guard) as a free alternative to PGP. GPG became part of the GNU project and used open standards.
- 2000s: GPG became a standard for many operating systems and development tools, as well as the basis for various applications and libraries that support encryption and digital signatures.
- Today: GPG is widely used for email security, authentication, and digital signatures in a variety of applications. It is supported by many operating systems and is part of many cryptographic solutions.
You need to have the recipient's public key to encrypt the file, and the recipient must have your public key to decrypt it. There is no danger in making your public keys just the public key
Public key (or Public key/Public key)
It's your digital business card. Share it with anyone you want to communicate with securely. Basically, it's your number for secure messaging.
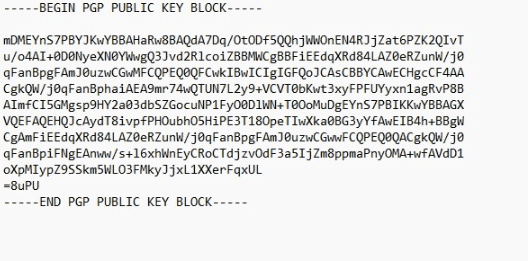
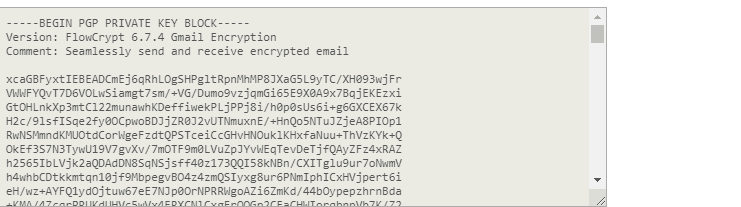
Private key
He needs to be watched closely. It deals with encrypting and decrypting messages. It is better to keep it in a safe place, for loss may cause problems.
GPG can be used for symmetric encryption, but its main application is in asymmetric data encryption. In a nutshell: in symmetric encryption, one key is used to encrypt and decrypt messages (e.g., a specific character corresponding to a specific letter). In the case of asymmetric encryption, two keys are used - a public key and a private key.
Symmetric Encryption: It is like a lock with one key. The same key is used to close and open the door. For example, if your friend sends you an encrypted message, you need the same key to read it.
Asymmetric Encryption: There are two keys, like two locks. One key (the public key) is used to encrypt messages and the other (the private key) is used to decrypt them. You can give the whole world your public key, and keep the private key secret. Only the owner of the private key will be able to unlock the "lock" and read the message. Simply put, if someone encrypts a message with your public key, only your private key will decrypt it.
So symmetric is one key for all operations, asymmetric is a pair of keys, each with its own role.
It's no secret that working through a terminal may not suit every person, and interacting with GPG in a Linux terminal can seem complicated and confusing.
We will look at an open source application designed to work with the GPG toolkit in a graphical shell. It is a godsend for beginners and those who prefer to avoid using the mysterious black command line window. Due to the cross-platform nature of the application, this article will be useful for Windows, Linux (Tails too) and FreeBSD users.
In various Unix-based operating systems, Cleopatra is easily accessible through repositories. For example, to install on Debian, just use the command:
sudo apt-get install kleopatra.If you prefer the Windows operating system, the program comes with the GPG4Win package.
The starting point of GPG is to create your own key pair. The public key can be distributed widely, while the secret key is stored in a secure location. The secret key is used to sign information on behalf of the owner and decrypt encrypted messages.

Here are a few of the benefits of using Kleopatra GPG:
- Kleopatra provides a graphical user interface, which makes working with GnuPG more convenient for those who prefer visual interaction.
- Kleopatra simplifies the creation, import, export and management of encryption keys. It allows users to easily add and remove keys and manage them in general.
- With Kleopatra you can easily encrypt and decrypt files without typing commands in the terminal. Just select the file, click on the appropriate item in the menu, and Kleopatra will perform the necessary steps.
- Kleopatra also makes it easy to sign documents using GnuPG. This is an important feature for data authentication.
- Kleopatra can integrate with some email clients to securely send and receive encrypted and signed emails.
- Kleopatra allows you to perform key certification operations, which increases the trust in your public key.
- Kleopatra provides reports on executed operations, which is useful for tracking and analyzing key and data activities.
- Kleopatra is available for a variety of operating systems including Windows and Linux, ensuring ease of use across platforms.
Open the terminal and enter:
sudo apt-get install kleopatra.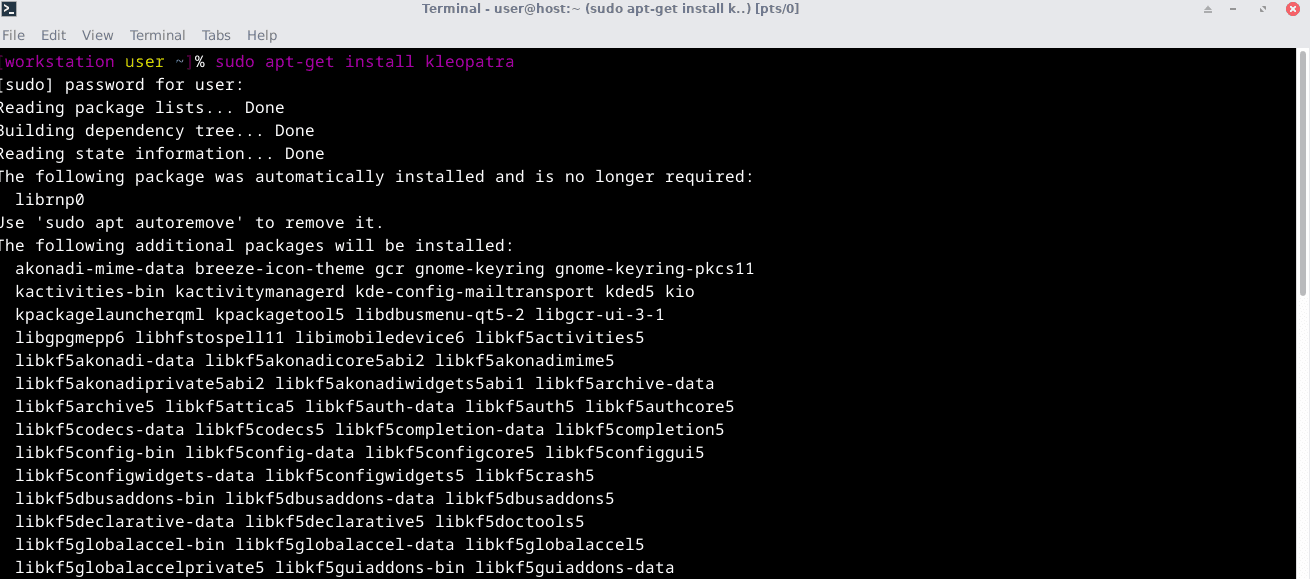
Update all packages after installation
Sudo apt-get updateRun it through the command:
Kleopatra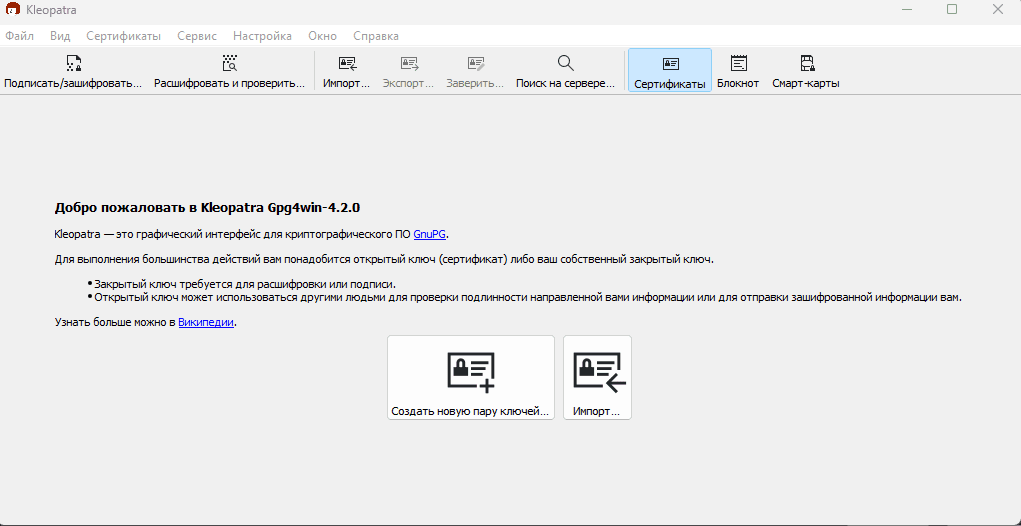
Go to the Gpg4win website and select the free version of GPG4WIN.
After that we are redirected to the page with automatic download of the file. Download and run it:
Once the setup is complete, you will see this window. Click "New Key Pair".
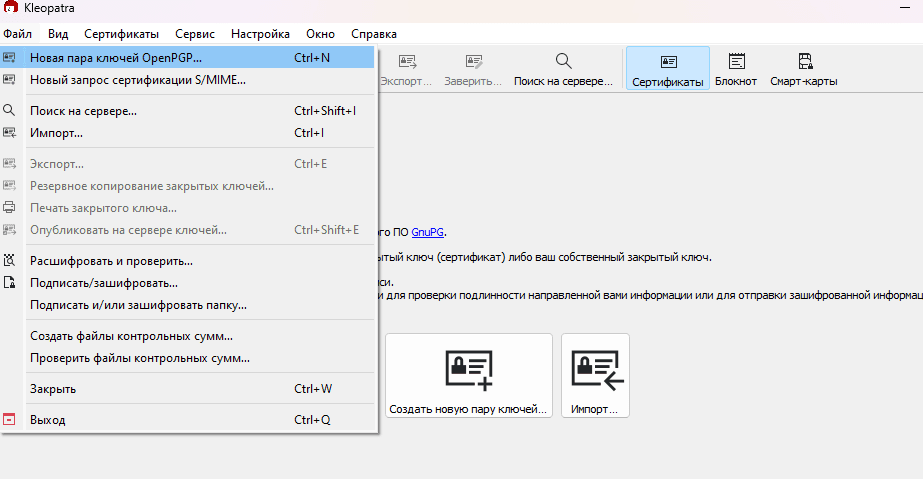
On the screen that appears below, enter your name and email address.
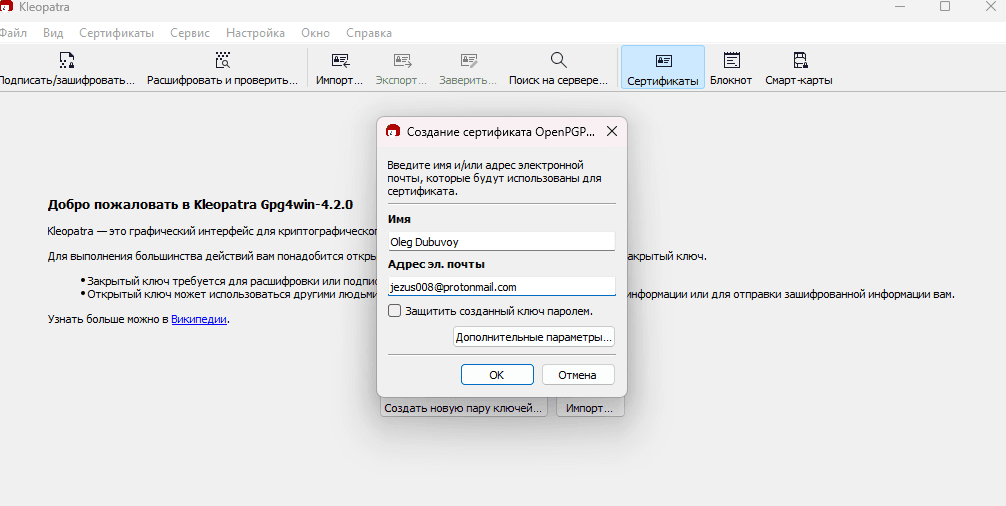
The password you enter does not participate in the encryption and decryption process; it serves as protection for your key, which is stored in a home folder on your computer. This password is necessary to prevent an attacker from accessing your private key in the event of physical access to your computer. An attacker will need to first guess or pick the password before they can use the private key. Therefore, it is important to create a strong password with different characters
Select additional parameters:
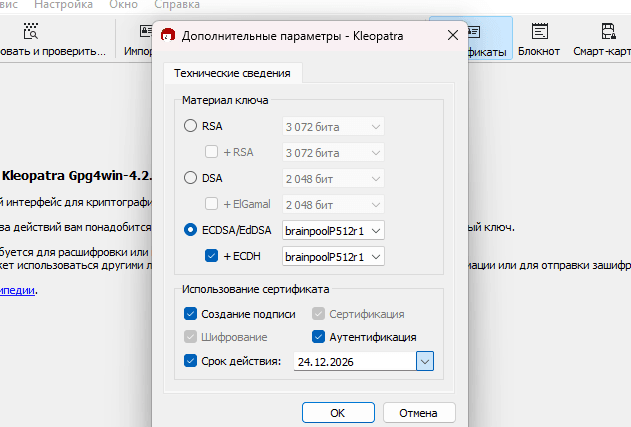
The default is RSA with a key of 2048 bits, but due to quantum technologies its reliability is decreasing. Elliptic curve algorithms such as brainpool provide high security with a shorter key length.
To create elliptic curve keys, choose ECDSA/EdDSA. Choose an algorithm, for example, brainpool. The key is created with an expiration date, which can be changed or disabled, making the key perpetual
Click on your profile (in our case Dmitrievich Oleg) and select details:
Select export
And we get our public key
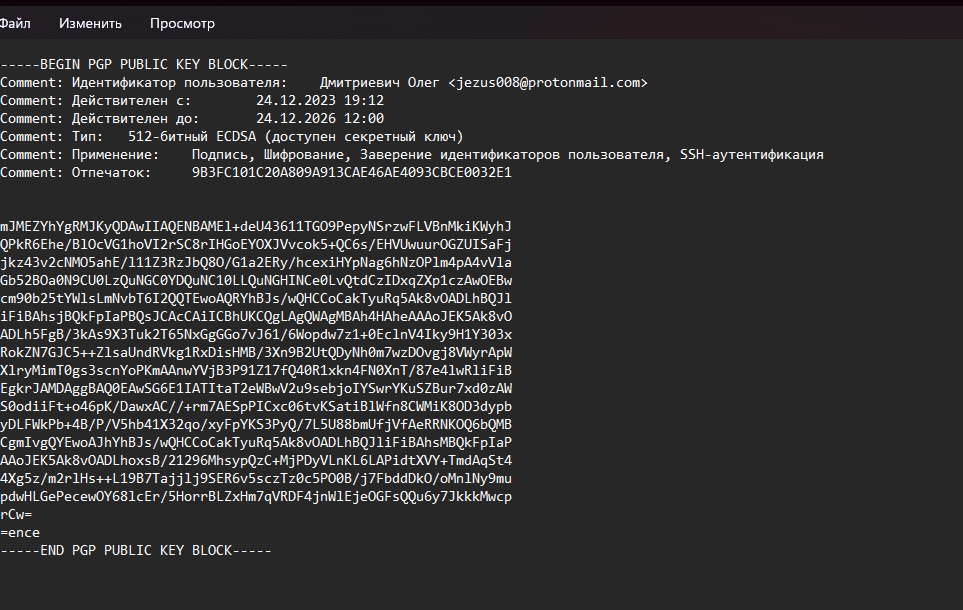
Right click on your profile and select "Backup private keys"
Save our key in a convenient place:

Open the file with a text editor:
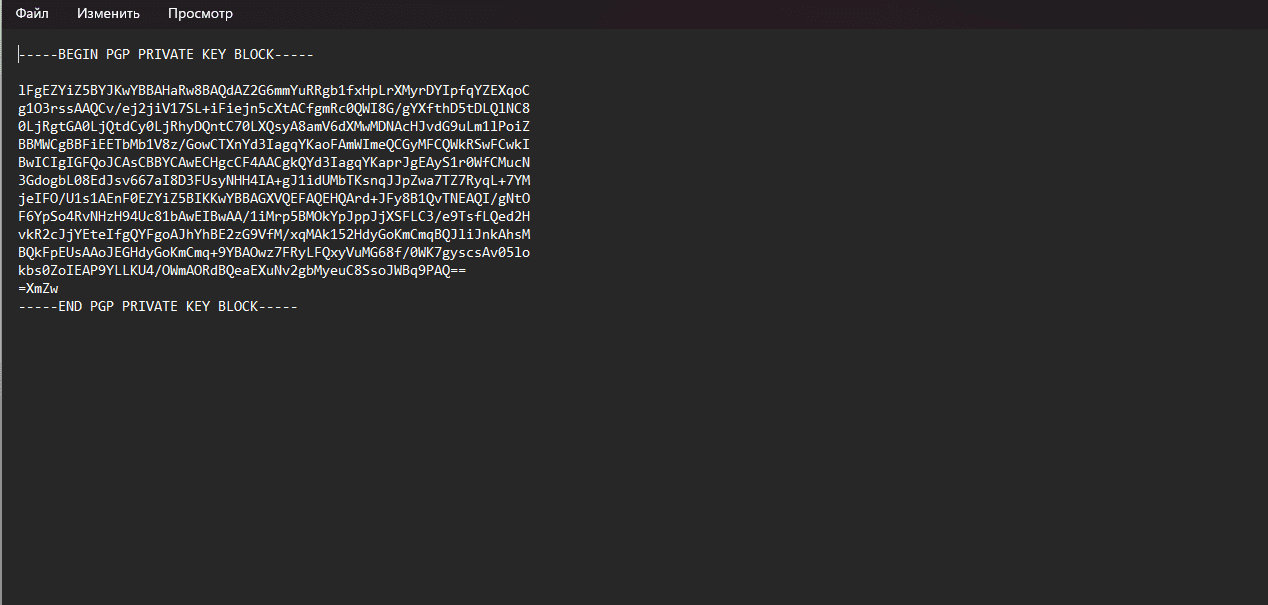
Now let's encrypt the message using Notepad in the Kleopatra program. We will encrypt the message only for ourselves, so that only we can read it.
Let's start by navigating to "Notepad" in the Kleopatra toolbar. Then type in your message.
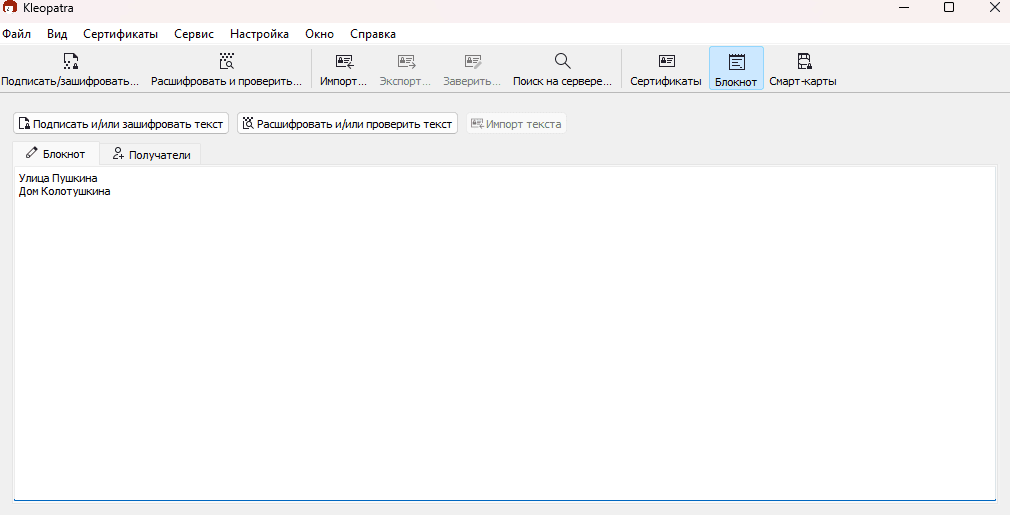
When your message is ready, you need to encrypt and sign it.
Click the "Recipients" tab.
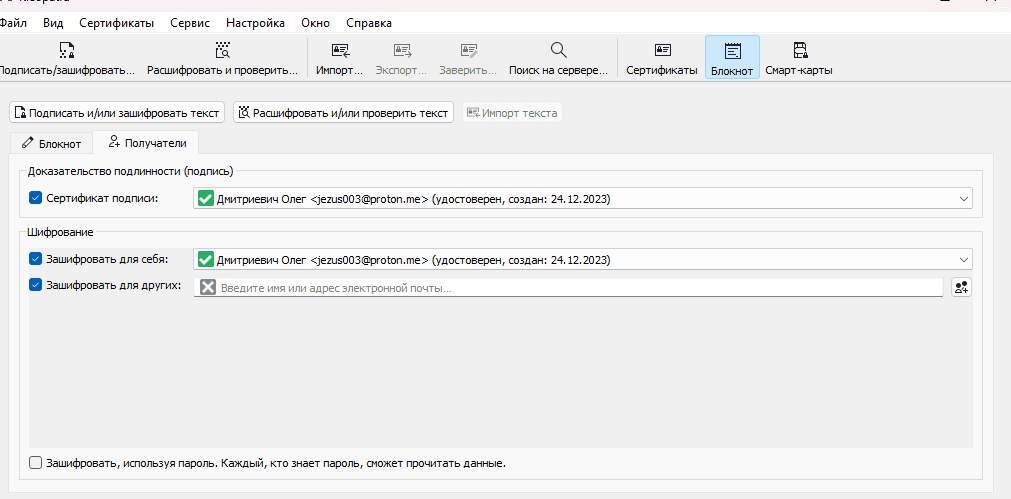
Since we are encrypting this message for ourselves, we will select the Encrypt for me option. We don't have any other recipients to encrypt messages for now, so we'll leave this option unchanged.
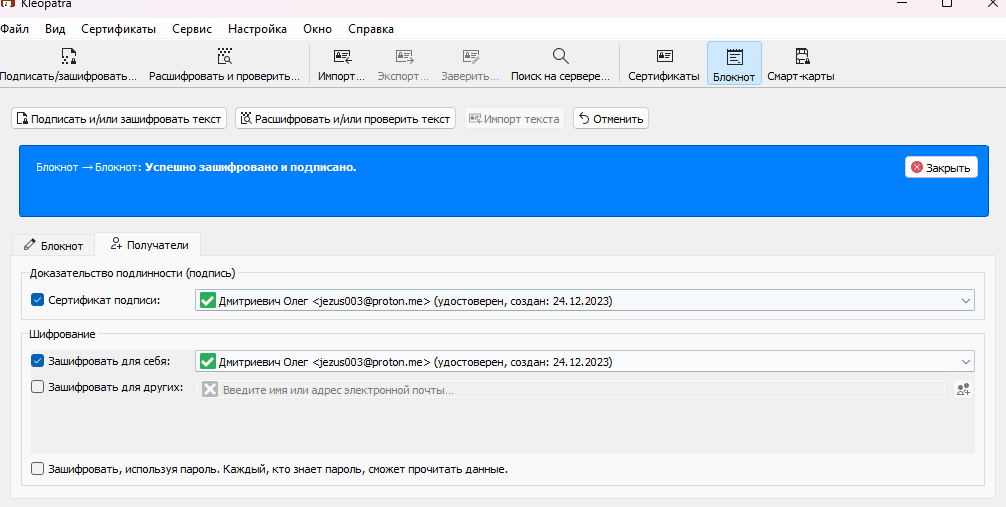
The successfully converted message is now a random string of incoherent text. You can copy/paste and save it anywhere, and only I can decrypt it back to the original message.
Now let's see how to decrypt an encrypted message back to its original state.
Suppose we have saved the message in a text file. Open Kleopatra, go to Notepad, and paste the encrypted message back into the text area.
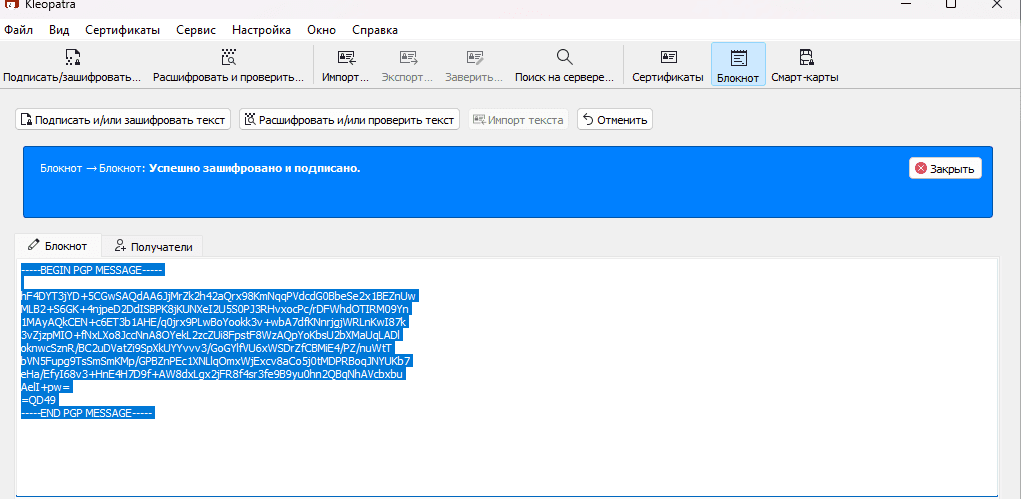
Since the message is sent only for myself, and my private key is securely stored on this computer, I can easily decrypt it by simply using the "Decrypt / Verify Notepad" button
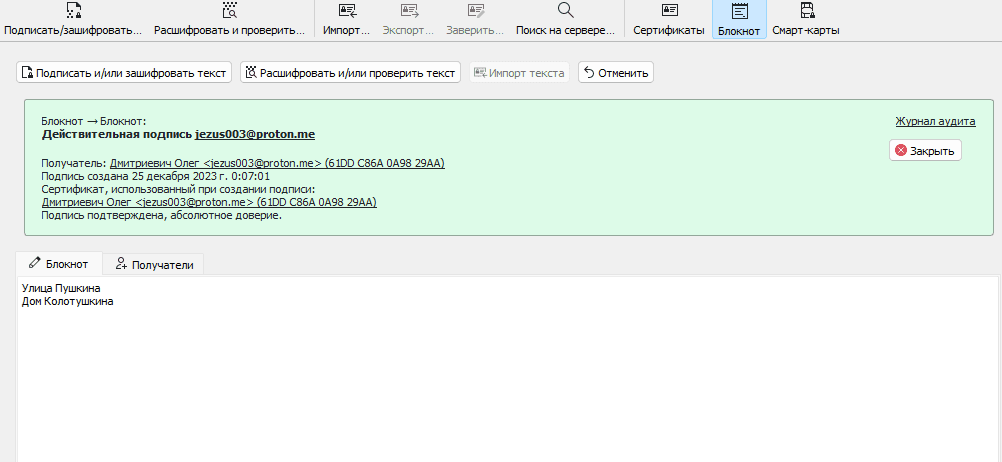
As you can see, the message has been decrypted. Since I "signed" the message on my behalf when encrypting it, it says "Valid signature from..." - so you can verify that the message is authentic and from the specified sender.
Let's do it again
To decrypt an encrypted message sent to you using your public key, you will need your own secret key. The process may be as follows:
- If you don't already have the sender's public key in Kleopatra, import it so that the application knows how to decrypt the message. You can import the key by opening the "File" tab and selecting "Import Certificates". Then specify the path to the public key file.
- Make sure that your secret key is added to Kleopatra. This is necessary so that the application can use it to decrypt messages. You can add a secret key through the "File" tab and selecting "Import Secret Keys".
- When you have the sender's public key and your secret key, Kleopatra should automatically use them to decrypt the message. Normally, if you have an encrypted message, just open it in Kleopatra and the program will automatically decrypt it using your keys.
Next, consider a situation where we want our friend to be able to send us an encrypted message. To do this, we must give him our public key. Remember that we never want to share our secret key with anyone else.
Go back to the Certificates page and select the key pair you want to use to receive messages from that person.
There are several ways to export a public key. We will export only the text. To do this, double-click on the key pair.
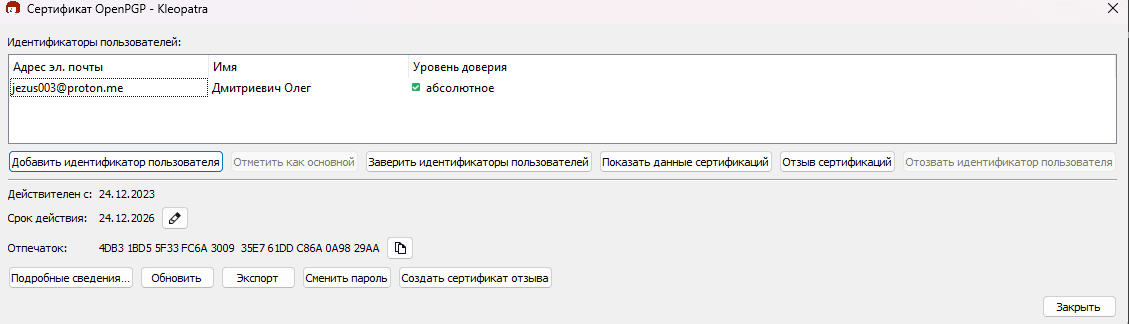
This will open a dialog box with additional information about the key. Click the Export button
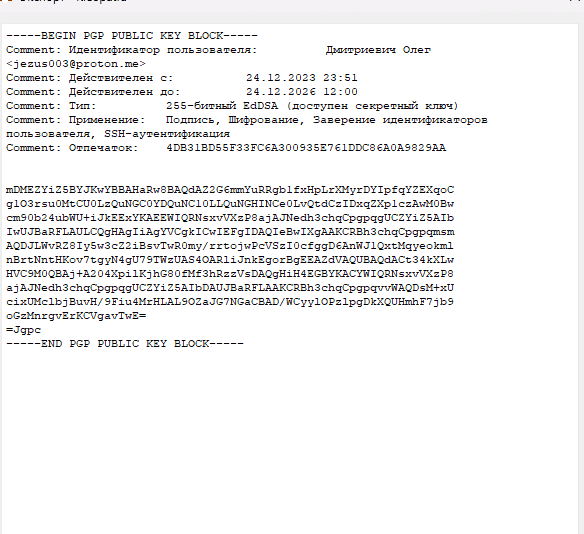
This is a public key block. You will share it with the people or services you want to receive encrypted messages from. This is what allows them to send you encrypted messages.
Once you send someone your public key, they will be able to send you messages. To decrypt messages sent to you, simply copy and paste them into notepad and decrypt them using your secret key as we did in the previous example (sending a message to yourself).
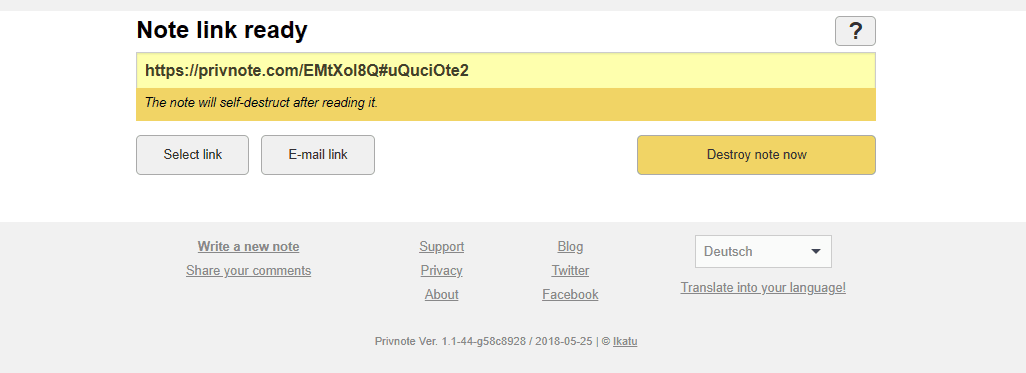
The easiest way to send it is through self-deleting messages.
Go to the Privnote website and send the text we need in the input field
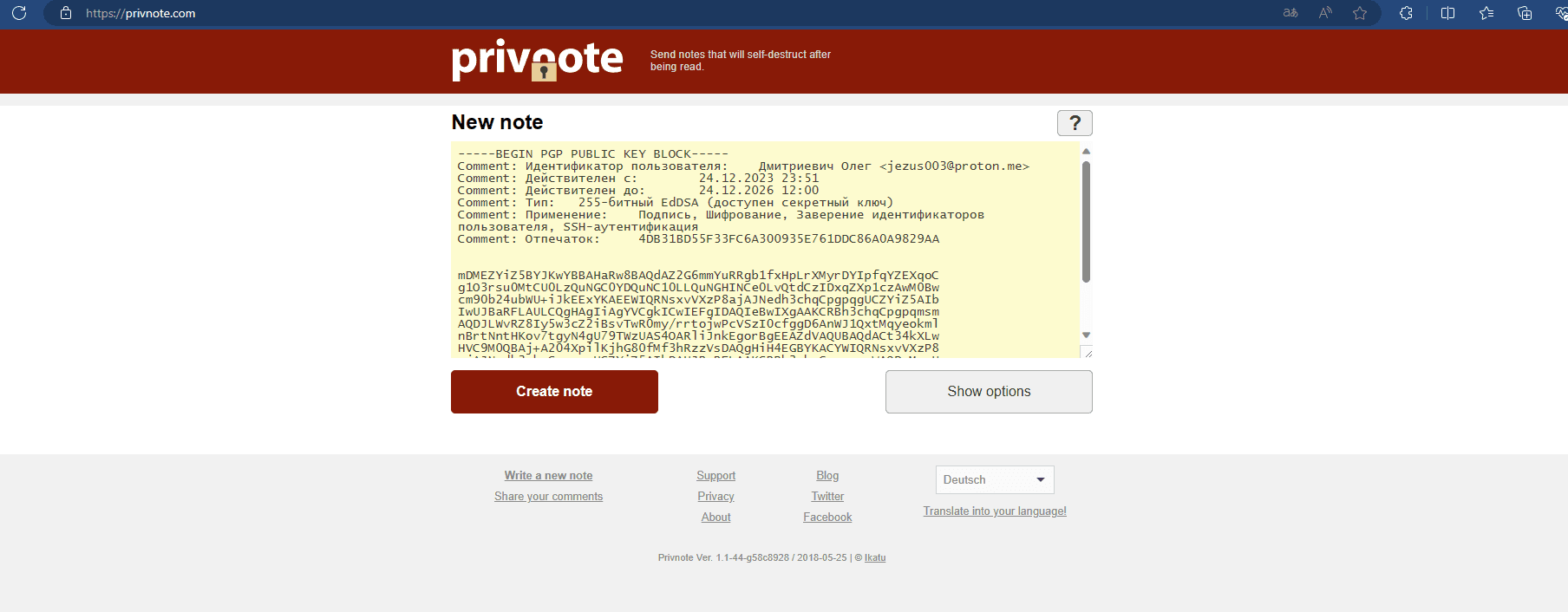
Now we have the possibility to send our key to the right recipient with a short link, the message will be deleted after reading it
Next, consider the situation where you are trying to send an encrypted message to someone else. To do this, they must provide you with their public key.
For demonstration purposes, here is our comrade's public key.
-----BEGIN PGP PUBLIC KEY BLOCK-----
Comment: Идентификатор пользователя: Kevin Agler <[email protected]>
Comment: Действителен с: 25.12.2023 2:05
Comment: Действителен до: 25.12.2026 12:00
Comment: Тип: 255-битный EdDSA (доступен секретный ключ)
Comment: Применение: Подпись, Шифрование, Заверение идентификаторов пользователя
Comment: Отпечаток: 07CC02E39730E43595FCE3CBBD40B56DDC7B8C61
mDMEZYi5HxYJKwYBBAHaRw8BAQdASxia8+gBW3whrcrcgbdE5f9TPzvOxj6NarIP
ceS7nQO0IktldmluIEFnbGVyIDxLZXZpbkBwcm90b25tYWlsLmNvbT6ImQQTFgoA
QRYhBAfMAuOXMOQ1lfzjy71AtW3ce4xhBQJliLkfAhsDBQkFpXdxBQsJCAcCAiIC
BhUKCQgLAgQWAgMBAh4HAheAAAoJEL1AtW3ce4xhQukBALAJD9lCfTrMYXP25Voa
b7nShxKJG5Xe3753V/PqHhRaAP9GHuOSJ5uKEeBHMxwLdCbDHfiwp+06ze4KEkAk
p6hbCLg4BGWIuR8SCisGAQQBl1UBBQEBB0AmsiL4iiGEN8l1BTiQPc8B0GBLOEFA
sIRFukAJTE3rYAMBCAeIfgQYFgoAJhYhBAfMAuOXMOQ1lfzjy71AtW3ce4xhBQJl
iLkfAhsMBQkFpXdxAAoJEL1AtW3ce4xhuWcBAOY82LteTn7jvAD+4XW78dkB56OG
pMjOrjzO44AhUXy1AQCYtsXJWwsTXAXjH4HnXhUbKVI1mKupdcS8SNIPd62aAg==
=LcFY
-----END PGP PUBLIC KEY BLOCK-----</[email protected]>The easiest way to import your public key is to save it as a text file. Open Notepad and paste my public key in there. Then save it as a .gpg file.
Paste the GPG key file we just created into Kleopatra. The program will ask if you want to "Confirm" the public key. If the key is confirmed, it means that you have verified the key fingerprint by comparing it with the fingerprint provided by the sender
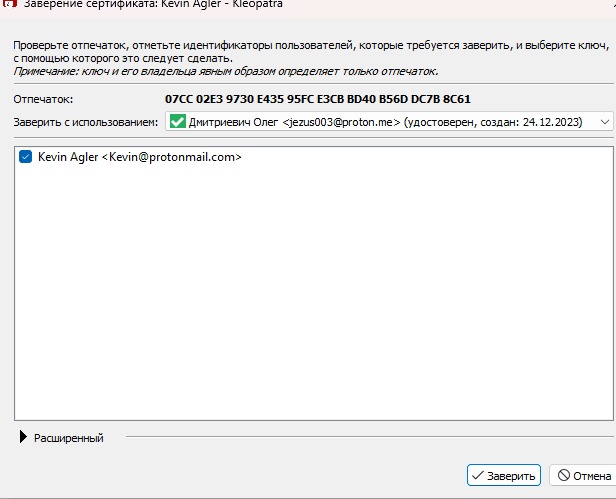
For example, you can contact the owner of the public key and ask them for a fingerprint of the key. If it matches the fingerprint they showed you, you can confirm that the key is genuine. Otherwise, someone has sent you an invalid or counterfeit key.
For our purposes, you can simply validate the key. The fingerprint must match "07CC02E39730E43595FCE3CBBD40B56DDC7B8C61".
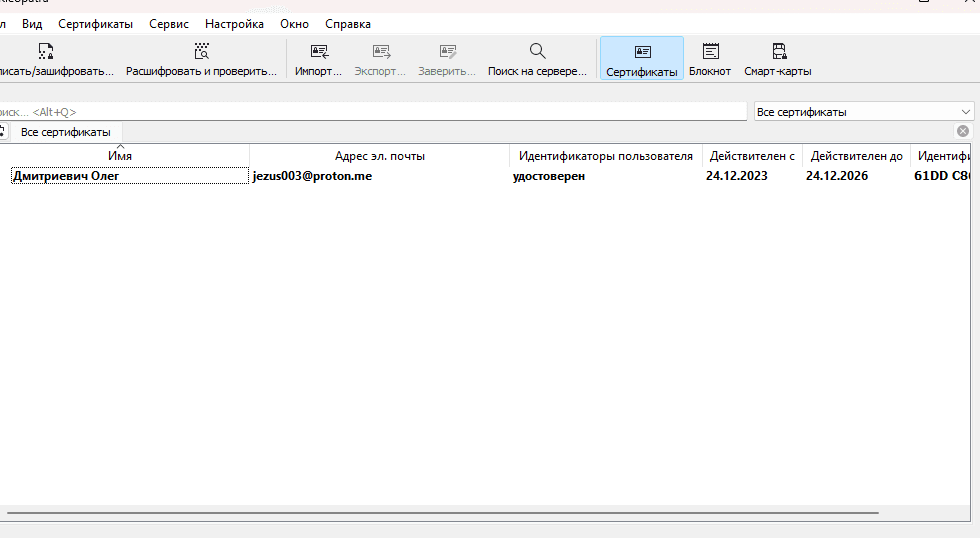
Now several keys will appear in the list of Kleopatra certificates. The first one should be your key pair, the second one should be the interlocutor's public key.
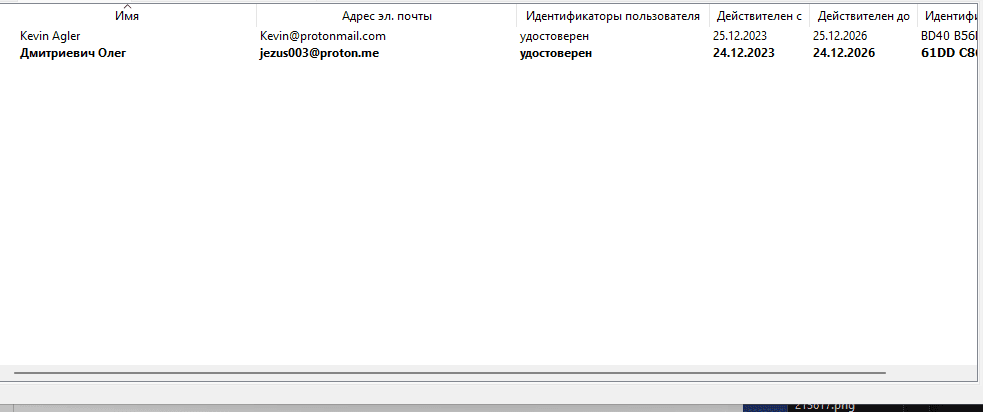
Back to the notepad. In this case, I have created a new key pair: private and public, for a person named "Billy Bob". Let's pretend that I am Oleg, and I need to send a message to Kevin. You can continue to use the private key you created earlier for yourself.
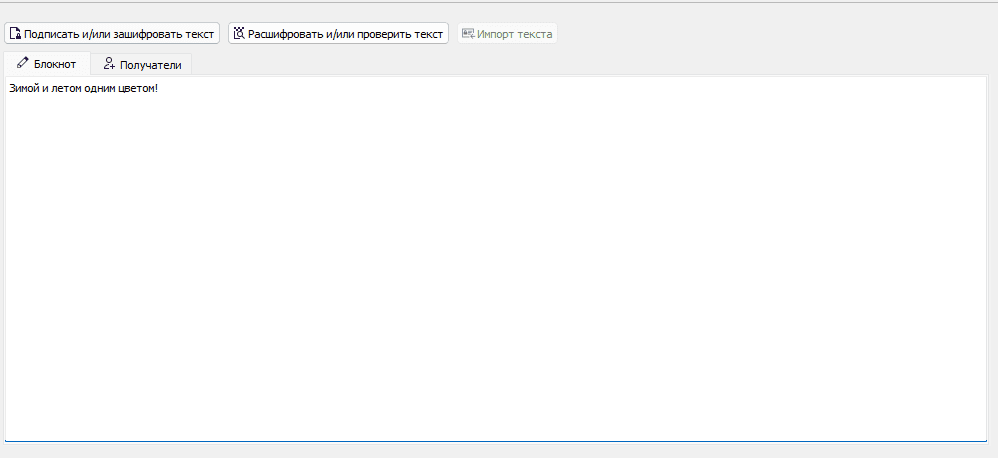
Enter the message you want only Kevin to see.
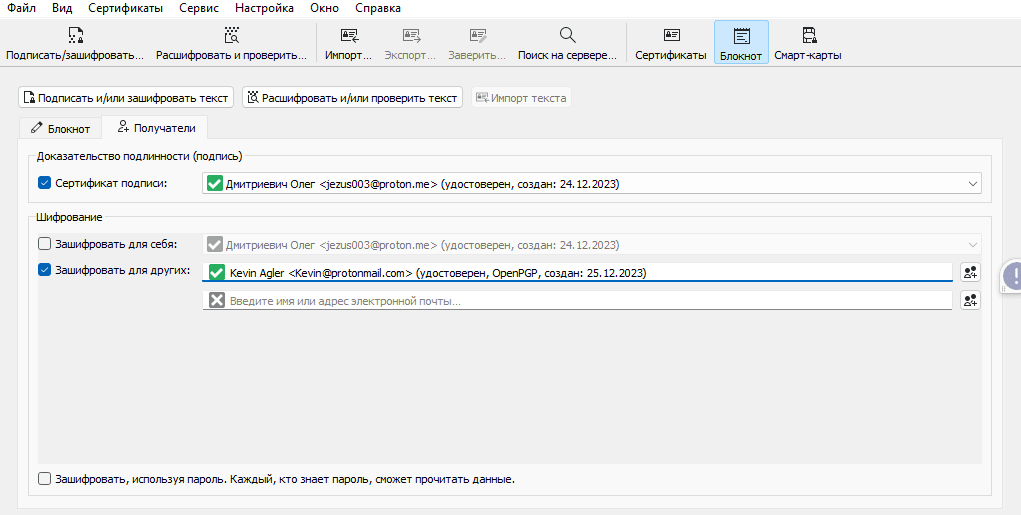
Click the Recipients tab. You can sign the message on your behalf if you want. In this example, I have disabled the "Encrypt for me" option. This means that once this message is encrypted, only the recipient will be able to decrypt it, and I will not be able to decrypt the message again by pretending to be Oleg.
Go to Notepad and click "sign".
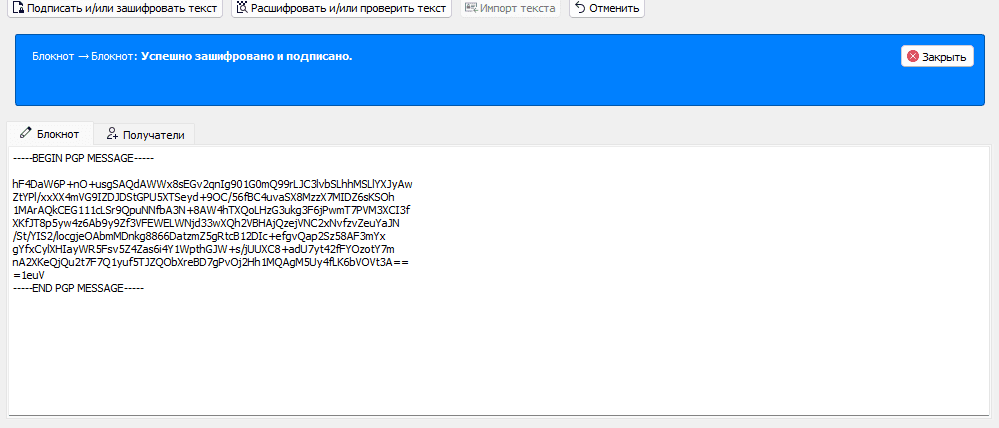
Now the message is encrypted. I can send it to anyone, but only Kevin can read it using his secret key.
If I try to decipher the message, it fails. Remember that in this example, I am "Oleg", not "Kevin". Only I can decrypt a message from Oleg using my secret key.
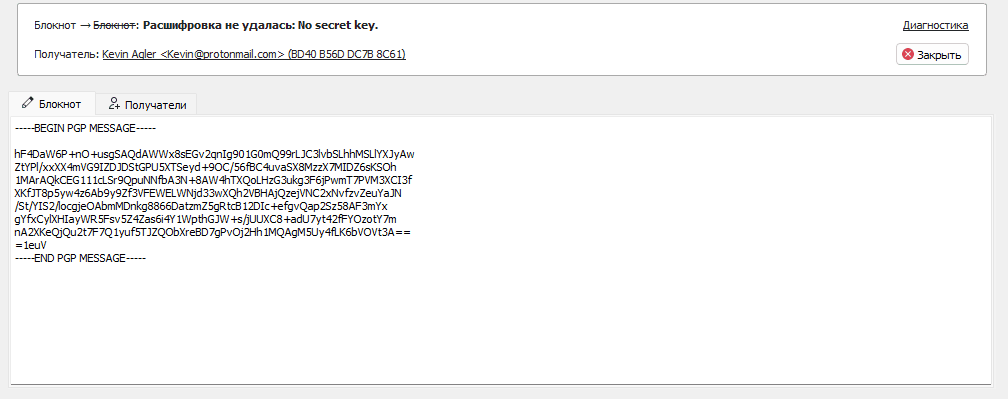
Now let's create a password protected message that can be read by anyone without a specific private key, as long as they know the password. To do this, go to Notepad and type your message.
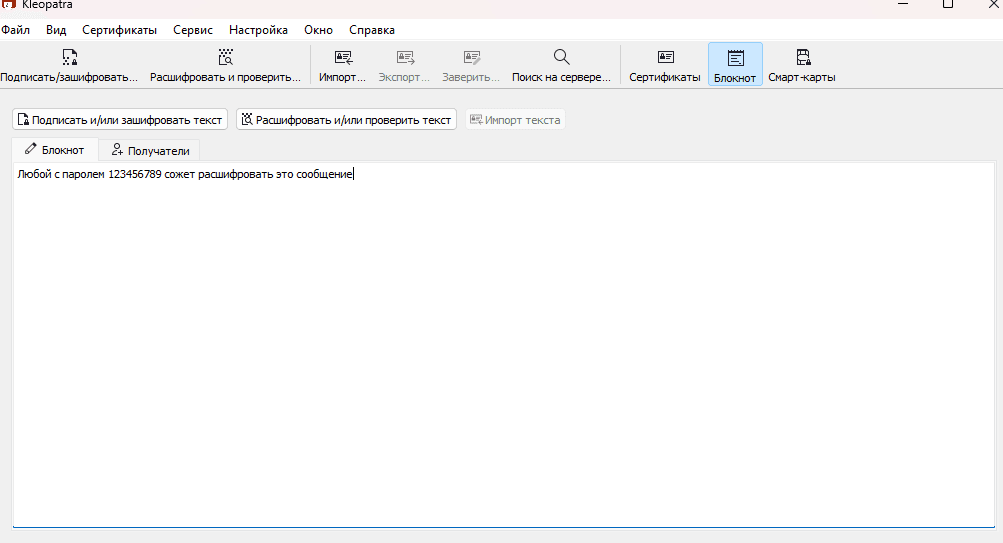
Navigate to the recipients and select the bottom "Encrypt with password" checkbox.
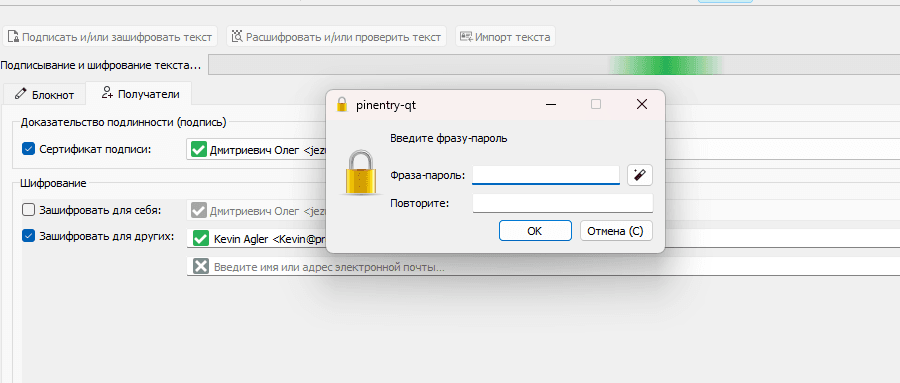
Enter the password and click OK
You can now decrypt the message by simply typing "mypassword". Anyone you send the message to will be able to decrypt it using this password. Note that this is much less secure than encryption/decryption using private/public keys.
Below will be our passworded message, you can decrypt it via the password 123456789
-----BEGIN PGP MESSAGE-----
hF4DaW6P+nO+usgSAQdABXYihZkXgKz5p0ERVqzDP2VufslzZpeLZdajMJ7ocz8w
F434Zf0BF0C0mMH0XB3VuI2XOrRdsDWOIfrxqQ10cC53lHq1FU6W8xqHbHKkuCsk
jE0FCQIDCM5KaJPTYChL/7VeiFnQ8cPKpYl9Tqh8fb2ct/GpVceXXXSQFQdzsL6V
C/DSHuyL0onuPSPkuMAdD8DHVI2lXxtKdHL6kxTiNtTAXgEJAhCYZavtd7ZwAQ8o
rHha9JiSfLhZIWtjttwRYg3Auar0ZCTvyy9S4V1j/yOeeiltdLeMENAMmTqvSqSz
d4ZXKBD0zQPihWq+VrkcaHP0X80JcKf6BVDQcaRtWfhRPDwUuJMBSeCdBBIIppj1
zuznkKiYf5Zlph4FczkIDLHCrEhsxw1G3I+qb5QXSV+C4VqNHENOTIQmLJB2PE19
5TAZZplNhtr6QSmX2MYXC7kcRRFQQyt6xCiuRjx5hs4Wabsagx+f9vvVzwRvPuVI
iQa+dEGlZmkvLc+XyeTqqgyFLV5NOX86G8N6oL1BPMiM/iqAYKmtAOz6a2Fl9S2W
PUAIRGLgoFb1yt+SxztHEi26U9jMY2fd5rdOR9duV4Y=
=GzY/
-----END PGP MESSAGE-----
If you want to distribute a public message but prove that it was you who wrote it, you can create a signed PGP message.
For example, we wrote the following message:
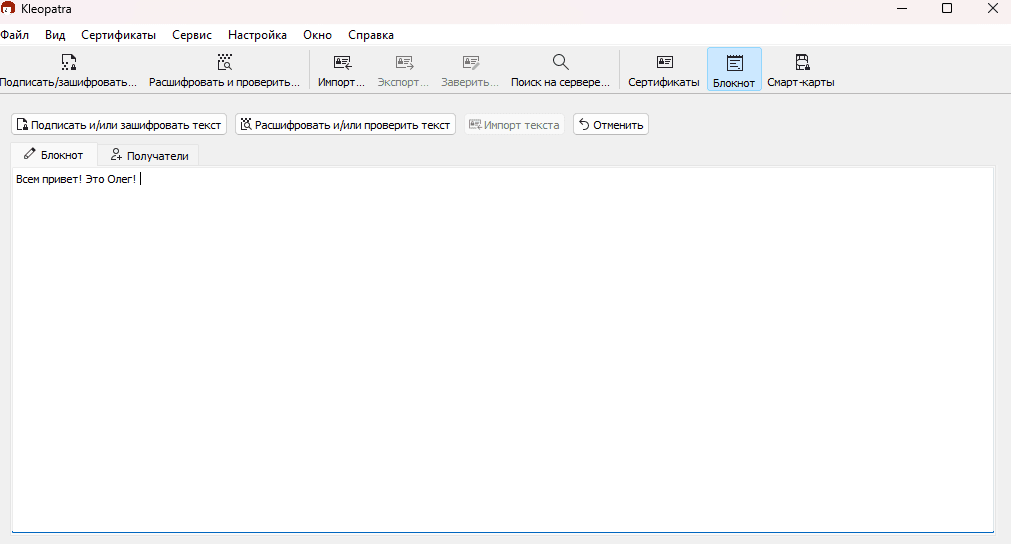
Now I'm going to "sign" the message without encrypting it myself.
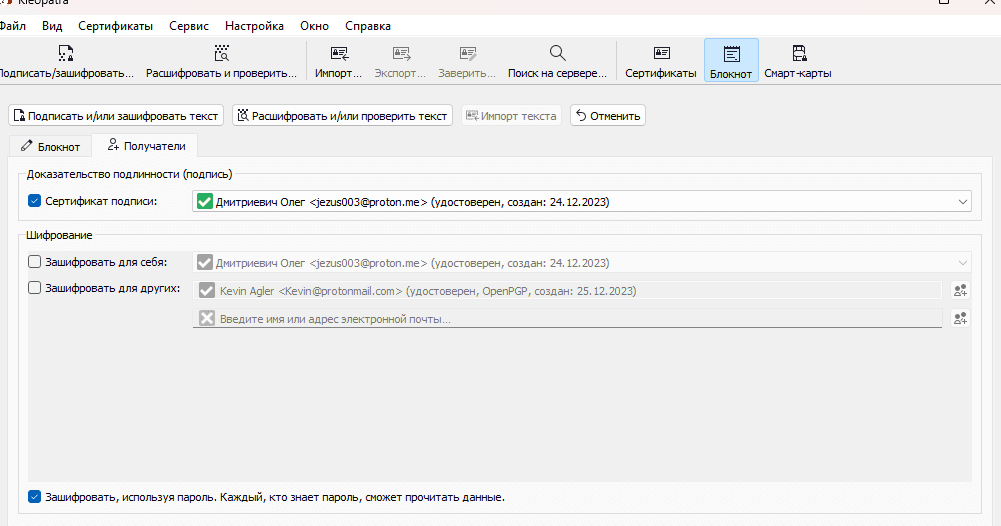
Now when I click on "Sign Notepad", I get the following output:
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA512
Всем привет! Это Олег!
-----BEGIN PGP SIGNATURE-----
iHUEARYKAB0WIQRNsxvVXzP8ajAJNedh3chqCpgpqgUCZYlv2wAKCRBh3chqCpgp
qviIAP9E08FGBrZSLlwl/CQWFtFtrqup75p36yTrRs6my13spAEA7Ngo5HBVW1Kf
BwaYRqEnvVFzebP8MW03eH2+/jNAUAo=
=dhGu
-----END PGP SIGNATURE-----
As you can see, the message itself is still visible. However, there is a PGP Signature section. Anyone with Kleopatra and my public key can paste this into notepad and click "Decrypt/Verify Notepad" - this will verify the PGP signature with my public key and notify them that the message has been validated.
You can verify the signature via decryption, but that requires saving my public key:
-----BEGIN PGP PUBLIC KEY BLOCK-----
Comment: Идентификатор пользователя: Дмитриевич Олег <[email protected]>
Comment: Действителен с: 24.12.2023 23:51
Comment: Действителен до: 24.12.2026 12:00
Comment: Тип: 255-битный EdDSA (доступен секретный ключ)
Comment: Применение: Подпись, Шифрование, Заверение идентификаторов пользователя, SSH-аутентификация
Comment: Отпечаток: 4DB31BD55F33FC6A300935E761DDC86A0A9829AA
mDMEZYiZ5BYJKwYBBAHaRw8BAQdAZ2G6mmYuRRgb1fxHpLrXMyrDYIpfqYZEXqoC
g1O3rsu0MtCU0LzQuNGC0YDQuNC10LLQuNGHINCe0LvQtdCzIDxqZXp1czAwM0Bw
cm90b24ubWU+iJkEExYKAEEWIQRNsxvVXzP8ajAJNedh3chqCpgpqgUCZYiZ5AIb
IwUJBaRFLAULCQgHAgIiAgYVCgkICwIEFgIDAQIeBwIXgAAKCRBh3chqCpgpqmsm
AQDJLWvRZ8Iy5w3cZ2iBsvTwR0my/rrtojwPcVSzI0cfggD6AnWJ1QxtMqyeokml
nBrtNntHKov7tgyN4gU79TWzUAS4OARliJnkEgorBgEEAZdVAQUBAQdACt34kXLw
HVC9M0QBAj+A204XpilKjhG80fMf3hRzzVsDAQgHiH4EGBYKACYWIQRNsxvVXzP8
ajAJNedh3chqCpgpqgUCZYiZ5AIbDAUJBaRFLAAKCRBh3chqCpgpqvvWAQDsM+xU
cixUMclbjBuvH/9Fiu4MrHLAL9OZaJG7NGaCBAD/WCyylOPzlpgDkXQUHmhF7jb9
oGzMnrgvErKCVgavTwE=
=Jgpc
-----END PGP PUBLIC KEY BLOCK-----
</[email protected]>Since I have my public key in Kleopatra, it can verify that the message was signed by Oleg and not some scammer.
I have a picture of my dogs, but it's top secret, so I want to prevent outsiders from accessing it.
If you have installed Kleopatra with context menu or shell extensions (which is the default option when installing Gpg4Win), you can right-click on the file you want to encrypt and select the "Sign and encrypt" option. On Windows 11, you may have to select the "Show more options" option first.
Select the key you want to use to sign the file and add the recipients you want to give access to the file. If you want the file to be accessible only to you using your secret key, simply select "Encrypt for me". In this example, I encrypted the file for myself and for Billy Bob.
Click the "Sign/Encrypt" button. The file is now encrypted.
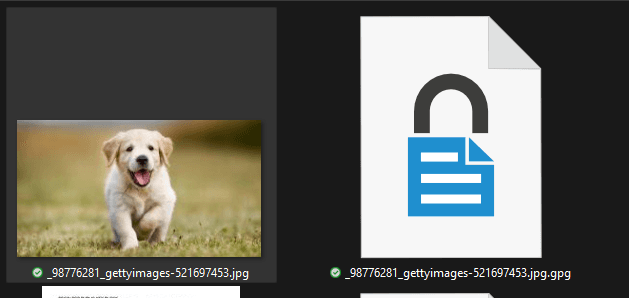
Now you can see that I have an original file and an encrypted file. I can send the encrypted file to anyone, but only me and Billy Bob can open it. I can post it publicly anywhere without fear of someone else seeing my cool puppy. If you encrypt files just for yourself, make sure you delete the original file after encrypting it!
To back up a key, simply right-click on the certificate in Kleopatra and select the "Backup secret keys" option. This will open a dialog box allowing you to save a backup key file.
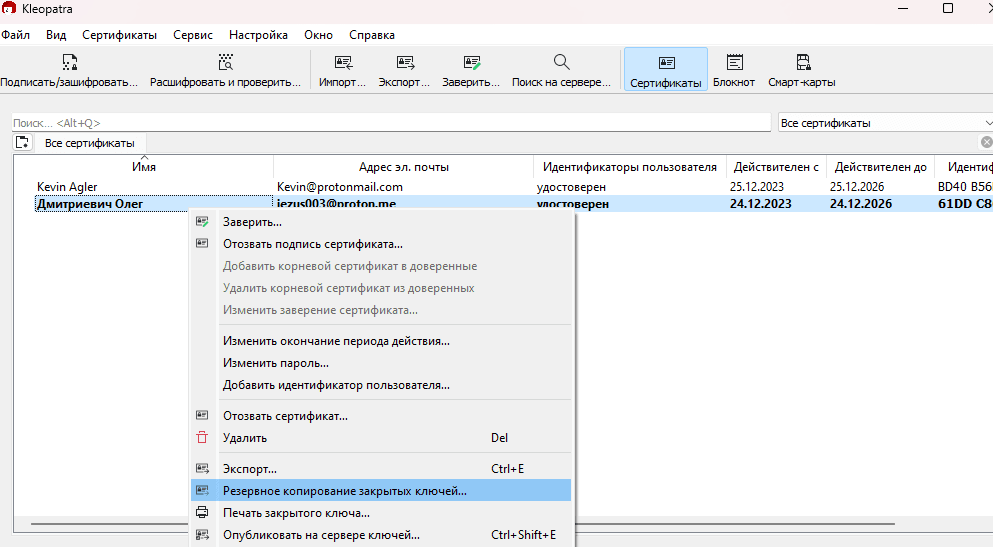
Save it in a safe place. If you need to recover the key later, you can import this secret key back into Kleopatra using the Import button.
Sending your public key to the key server in Kleopatra is an important step to ensure the secure exchange of encrypted messages. Public keys are essential for encrypting messages, and having them on the key server brings several benefits:
- Key availability to other users: Placing your public key on the server makes it available to anyone who wants to send you an encrypted message. This simplifies the key exchange process, because other users do not need to specifically request your key - they can get it from the server.
- Key Update and Revocation: If you need to update your key or revoke it, sending new version or revocation information to the server helps other users keep up to date with changes.
- Centralized access: The Key Server serves as a centralized resource for finding and retrieving public keys, making the key exchange process more convenient and efficient.
This process keeps key information transparent and up-to-date, which is an important element of public key cryptography. Sending the public key to the server contributes to the simplicity and security of encrypted communications.
Comments
ads



